HowTos: Difference between revisions
| (109 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
= | =Getting started= | ||
NEW! | |||
The first edition of "Wireless Networking in the Deveolping World" is available as e-book now. Prints can be ordered on demand at lulu.com. | |||
The e-book is available at no cost under a creative commons license. | |||
Get your copy at [http://wndw.net/ wndw] or [[Media:Wndw-ebook.pdf|locally]] and share it. | |||
==Step 1. Check where you are on the planet:== | |||
Your very first step is to find your current position on a map and then see what other wireless nodes are nearby. The best way to do this is to get a GPS and find out your coordinates and then to enter these into [http://earth.google.com/ google earth] - you can also use google earth to find your coordinates by identifying your house on the satellite image. | |||
==Step 2. Check who else is around that you can connect to == | |||
Once you have entered your google earth position - have a look at the positions of other wifi installations around you. For the [[Pretoria Mesh]] we have stored all the google earth positions in this [ftp://ftp.icomtek.csir.co.za/pub/in/wiki/wifi%20installations.kmz file]. You can also have a look on sites like [http://http://www.nodedb.com/ NodeDB] to see if there are other wireless installations near you. Once you have identified someone that you want to connect to, the best way to check connectivity is to use a WiFi sniffer such as [http://www.netstumbler.com/ netsumbler] for windows or [http://www.kismetwireless.net/ Kismet] on linux loaded on a laptop with a Wifi card fitted with an external antenna. For people in Pretoria we have a kit like this that can be borrowed from our WiFi tuckshop. Find the highest point at your house such as your roof and slowly rotate the directional antenna around you to see if you can pick up any WiFi access points. You will want to find an access point that is in ad-hoc mode and is mesh enabled - the wifi sniffer will tell you if the wireless node is in ad-hoc mode but you will have to contact the owner to check what mesh protocol, if any, they are running. | |||
==Step 3. Build a mesh node== | |||
Now that you know where you are located and you have hopefully found someone you can connect to, you will need to construct your mesh hardware. | |||
A mesh network node consists of a wireless router, antenna, routing software and settings. | |||
[[ | ===[[Wireless Router]]=== | ||
Your wireless router can either be a PC with a wireless card, a dedicated [[Wireless Router]] unit or [[SBC]] Single Board Computer with a wireless card. A dedicated [[Wireless Router]] is the most popular choice because it is relatively cheap, easy to configure and low power making it practicle for a device that is meant to be on most of the time. Have a look at [[Cost Tables]] to get an idea of all the possible types of mesh nodes you can build together with the cost implications | |||
===Antennae:=== | |||
The first step is to select an antenna that suits your situation best. There are several types of Antennae: | |||
1) [[Omnidirectional]] | |||
2) [[Yagi-Uda]] | |||
3) [[Grid]] | |||
4) [[Flat-panel]] | |||
5) [[Wave-guide]] | |||
The main difference between these antennae is the [[Radiation Pattern]]. Each type is also available with different [[Gain]] specifications. | |||
Typical [[Wireless Router]]s are sold with 2 omnidirectional antennae and these can be re-used as part of your node, depending on your situation. If you have other nodes in your vicinity that are spread out in all directions but are fairly close (i.e. < 3Km), then an omni-directional antenna should suffice. If the other nodes are concentrated in one direction, for example, if you have a hill on one side of your house and theres no point in radiating the hill, then you may want to choose a more directional antenna, like a 180 degree [[Flat-panel]]. For point-to-point links, a smaller radiation angle is needed and [[Grid]] or [[Yagi-Uda]] type antennae are probably best suited. | |||
==Step 4. Install latest mesh networking firmware== | |||
The type of software that needs to be installed will typically be implmentations of mesh routing protocols like [[OLSR]], as well as security software, like VPN clients. On dedicated wireless routers, this is typically implemented on Firmware, while on standard PC's its implemented in Software. | |||
===[[WRT54G]] Firmware update=== | |||
[[Wireless Router]]s like the [[WRT54G]] are not mesh capable as is. One of the reasons for selecting the Linksys is that the Firmware is upgradeable. | |||
'''Caution: ''' Please note, that fiddling with the firmware will void your warranty!!! | |||
The following instructions apply to networks running the OLSR routing protocl, like the [[Pretoria Mesh]]. | |||
1. Download freifunk firmware from [http://www.freifunk.net/wiki/FreifunkFirmwareEnglish Freifunk site] or [ftp://comgingsoon Local] | |||
2. Set boot wait on linksys | |||
Web method: | |||
Navigate to web page were you can send pings and type each of these lines one line at a time | |||
;cp${IFS}*/*/nvram${IFS}/tmp/n | |||
;*/n${IFS}set${IFS}boot_wait=on | |||
;*/n${IFS}commit | |||
;*/n${IFS}show>tmp/ping.log | |||
NVRAM method: | |||
telnet into box and type the following | |||
nvram set boot_wait=on | |||
nvram commit | |||
reboot | |||
3. Upload firmware | |||
Give yourself a fixed IP in the 192.168.1.x range e.g. 192.168.1.100 | |||
Use tftp to upload firmware | |||
tftp 192.168.1.1 | |||
tftp> binary | |||
tftp> rexmt 1 | |||
tftp> trace | |||
Packet tracing on. | |||
tftp> put openwrt-g-freifunk-1.0.2-en.bin | |||
Wait for the power light to stop flashing | |||
Power cycle the box | |||
==Step 5. Install mesh node== | |||
===HowTo Water-proof your equipment=== | |||
[[Image:Usb-wireless-final.jpg|thumb]] | |||
[[Image:Wireless-router-outdoor1.jpg|thumb]] | |||
==Step 6. Setup mesh configuration== | |||
1. Check that the web interface is working. Visit the site http://192.168.1.1 on your web browser - you should see the main freifunk web interface appear | |||
2. Set up the wireless interface | |||
WLAN protocol: Static | |||
Ip Address: 192.168.2.5 | |||
Netmask: 255.255.255.0 | |||
WLAN Mode: Ad Hoc (Peer to Peer) | |||
ESSID: mesh | |||
Channel: 6 | |||
TX Power: 100 | |||
3. Set up the LAN interface | |||
LAN protocol: Static | |||
LAN IP: 192.168.4.1 | |||
LAN Netmask: 255.255.255.0 | |||
Disable NAT: yes | |||
Disable Firewall: yes | |||
4. Set up the WAN interface | |||
WAN Protocol: DHCP | |||
Host name: Lawrence | |||
5. Set up OLSR | |||
HNA4: 192.168.4.1 255.255.255.0 | |||
6. Restart the Linksys | |||
You should now be given an IP address in the 192.168.3.x range | |||
You should be able to connect to another mesh access point and even get a default gateway to an internet point, if one exists | |||
You | |||
192. | |||
==Step 7. Start surfing== | |||
Hopefully you`re now hooked up to the internet and you can start surfing the web or hooking up to other PCś on the mesh | |||
==Step 8. Troubleshoot== | |||
Start with Layer 1: | |||
Is everything switched on? | |||
Is the LAN plugged in? | |||
Is the Antenna connected? | |||
Is it facing the right direction? | |||
Is it polarised correctly? | |||
Check software settings: | |||
Is the correct antenna selected? | |||
Is the routing daemon running? | |||
=[[WRT54G]] HowTos= | =[[WRT54G]] HowTos= | ||
==HowTo choose which antenna port to use on the WRT54G for an external antenna== | |||
Where to connect the external antenna | |||
WRT54g v1, v1.1, v2 | |||
look at the backside and connect the external antenna to the right antenna connector | |||
WRT54g v2.2 v3 3.1 v4 and the WRT54GL v1.0 | |||
look at the backside and connect the external antenna to the left antenna connector | |||
==HowTo create an ipk package== | ==HowTo create an ipk package== | ||
| Line 109: | Line 223: | ||
Without the “-c” option, I could not get the package installed successfully, you can try with or without and see for yourself. | Without the “-c” option, I could not get the package installed successfully, you can try with or without and see for yourself. | ||
==HowTo run Kismet on a WRT54G== | |||
*Install either the kismet or kismet_drone package. | |||
*Edit /etc/kismet_drone.conf and change the source from wrt54g,eth1,wrt45g to wrt54g,prism0,wrt54g. | |||
*Run kismet from your host, pc and off u go! | |||
==HowTo check your Linksys WRT54G version== | ==HowTo check your Linksys WRT54G version== | ||
| Line 137: | Line 256: | ||
{| style="width:400px; height:200px" border="1" | {| style="width:400px; height:200px" border="1" | ||
|- | |- | ||
| Model | | Model | ||
| S/N | | S/N | ||
| Line 144: | Line 262: | ||
|- style="height:100px" | |- style="height:100px" | ||
| WRT54G v1.1 | | WRT54G v1.1 | ||
| CDF20xxxxxxx | | CDF20xxxxxxx CDF30xxxxxxx | ||
| (./) | | (./) | ||
| (./) | | (./) | ||
|- | |- | ||
| WRT54G v2 | | WRT54G v2 | ||
| Line 153: | Line 270: | ||
| (./) | | (./) | ||
| (./) | | (./) | ||
|- | |- | ||
| WRT54G v2.2 | | WRT54G v2.2 | ||
| Line 159: | Line 275: | ||
| {X} | | {X} | ||
| (./) | | (./) | ||
|- | |- | ||
| WRT54G v3 | | WRT54G v3 | ||
| Line 165: | Line 280: | ||
| {X} | | {X} | ||
| (./) | | (./) | ||
|- | |- | ||
| WRT54G v3.1 (AU?) | | WRT54G v3.1 (AU?) | ||
| Line 171: | Line 285: | ||
| {X} | | {X} | ||
| (./) | | (./) | ||
|} | |} | ||
| Line 238: | Line 351: | ||
|- | |- | ||
|WRT54G v1.1 | |WRT54G v1.1 | ||
| | |||
|bcm94710dev | |bcm94710dev | ||
| | |||
| | |||
|42 | |42 | ||
|5 | |5 | ||
|BCM4710 V0.0 | |BCM4710 V0.0 | ||
|- | |- | ||
WRT54G v2.0 | |WRT54G v2.0 | ||
| | | | ||
|0x0101 | |0x0101 | ||
| Line 298: | Line 414: | ||
|- | |- | ||
|WRT54GS v1.1 | |WRT54GS v1.1 | ||
0x10 | |0x10 | ||
0x0708 | |0x0708 | ||
0x0318 | |0x0318 | ||
0 | |0 | ||
42 | |42 | ||
| | |||
| | |||
|- | |- | ||
Buffalo WBR-54G | |Buffalo WBR-54G | ||
0x10 | |0x10 | ||
bcm94710ap | |bcm94710ap | ||
0x0188 | |0x0188 | ||
2 | |2 | ||
42 | |42 | ||
| | |||
| | |||
|- | |- | ||
Toshiba WRC1000 | |Toshiba WRC1000 | ||
| | |||
bcm94710r4 | |bcm94710r4 | ||
| | |||
| | |||
100 | |100 | ||
| | |||
| | |||
|- | |- | ||
Buffalo WBR2-G54S | |Buffalo WBR2-G54S | ||
0x10 | |0x10 | ||
0x0101 | |0x0101 | ||
0x0188 | |0x0188 | ||
0 | |0 | ||
00 | |00 | ||
| | |||
| | |||
|- | |- | ||
Asus WL-500G Deluxe | |Asus WL-500G Deluxe | ||
0x10 | |0x10 | ||
bcm95365r | |bcm95365r | ||
| | |||
| | |||
45 | |45 | ||
5 | |5 | ||
BCM3302 V0.7 | |BCM3302 V0.7 | ||
|- | |- | ||
|} | |} | ||
| Line 365: | Line 481: | ||
3. Lock the RX and TX antenna to the one you connected your external antenna too, don't use AUTO. TAKE NOTE!!! On Version 2.0 hardware Antenna A is on the left looking from the front of the linksys and and on Version 2.,2 hardware Antenna A is on the right looking from the fron of the linksys. This caught me out a few times. | 3. Lock the RX and TX antenna to the one you connected your external antenna too, don't use AUTO. TAKE NOTE!!! On Version 2.0 hardware Antenna A is on the left looking from the front of the linksys and and on Version 2.,2 hardware Antenna A is on the right looking from the fron of the linksys. This caught me out a few times. | ||
==HowTo configure netmasks on OLSR/Freifunk== | |||
I had this problem with the OLSR web interface on the Freifunk openwrt implementation. If entered the following for the HNA4 field | |||
HNA4: 10.3.13.1 255.255.255.0 | |||
Which should advertise the whole 10.3.13.x net it would advertise the 10.0.0.0 net. I discovered that it needs the subnet mask in this format instead | |||
HNA4: 10.3.13.1/24 | |||
A few other things I learnt | |||
1. NVRAM variable ff_hna4 stores the HNA4 setting | |||
2. /etc/olsr.conf is ignored by freifunk | |||
3. /rom/etc/olsrd.conf stores a permanent copy of the olsrd setup | |||
4. /var/etc/olsrd.conf is a symbolic link to /tmp/etc/olsrd.conf ... this file is copied from /rom/etc/olsrd.conf into RAM (ramfs filesystem) and is the one called by olsrd. | |||
ps -A will reveal that olsrd is called as follows | |||
olsrd -f /var/etc/olsrd.conf -d 0 | |||
==HowTo Brick and De-Brick a WRT54G== | |||
Theres nothing like learning the hard way! As a result of my usual "If it ain't broke, it hasn't been fixed enough" approach to life, I fiddled with the Linksys until it innevitably went into a coma/ vegetative state. How did I manage this you ask? Simple, I started by doing a firmware upgrade using the wrong sveasoft image, which resulted in a moderately upset linksys which refused to talk to me on the web interface. With the help of our trusted Android (Andrew), I managed to do a reset-hold/ ping / tftp recovery and then flashed the poor bugger with OpenWRT, which according to OpenWRT is still not supported by them for the version 2.2 Linksys, which I subsequently found out I was using! So alas, all that remained was a perfectly dead Linksys, not responding to anything. It was time to go in, screwdrivers a blazing. I shorted out pins 15 and 16 and started up the Linksys, this created a crc error which was detected on boot, this then started up an emergency TFTP server which allowed me to ping and finally tftp the original Linksys firmware back onto it! | |||
More details on the recovery processes can be found here: | |||
[http://openwrt.org/OpenWrtDocs/Troubleshooting OpenWrtDocs/Troubleshooting - OpenWrt] | |||
Whew! | |||
==How to set up Linksys as a RIP2 router with client mode== | |||
How to set up Linksys as a RIP2 router with client mode | |||
1. Load Alchemy pre-release 5.2.3 onto the linksys | |||
2. Set the Linksys Wireless interface to Client mode and set SSID to "pta-mesh" | |||
Using the web interface select Wireless - Basic Settings | |||
Wireless Mode : Client | |||
SSID: pta-mesh | |||
Select Save Settings - continue | |||
3. Choose your IP addresses for the Wireless interface and the LAN interface | |||
I chose the following | |||
WAN interface: 10.50.1.13 | |||
LAN interface: 10.3.11.1 | |||
Using the Web interface select Setup - Basic Setup | |||
Internet Connection Type: Static IP | |||
Internet IP Address: 10.50.1.13 | |||
Subnet Mask: 255.255.255.0 | |||
Router Name: Something you like eg. david_home | |||
Local IP Address: 10.3.11.1 | |||
Subnet Mask: 255.255.255.0 | |||
Select Save Settings - continue | |||
4. Add router configuration files to the target directory | |||
Enter the router directory ($LINKSYS/src/router) | |||
# cd /mipsel-uclibc/target | |||
# mkdir /usr/local | |||
# mkdir /usr/local/etc | |||
Download my RIP configuration files for linksys | |||
ripd.conf | |||
zebra.conf | |||
Copy these files to $LINKSYS/src/router/mipsel-uclibc/target/usr/local/etc | |||
Download my image making script which will build files in the code.bin image | |||
makeimage.sh | |||
Copy this script to $LINKSYS/src/router | |||
Run the script | |||
./makeimage.sh | |||
You should now have a code.bin with the router config files in /usr/local/etc | |||
Upload this new firmware to the linksys | |||
5. Add commands to rc_startup to startup RIP, Flush iptables (so that RIP messages can arrive on RIP port) and remove NAT | |||
zebra -d -f /usr/local/etc/zebra.conf | |||
ripd -d -f /usr/local/etc/ripd.conf | |||
iptables -F | |||
iptables -F -t nat | |||
8. You should now have a rip enabled linksys client - Try ping the network connected to the wireless interface from a machine connected to the LAN | |||
Things to improve in this recipe | |||
1. Don't flush all iptables - just enable the port for RIP routing | |||
2. Find location in Makefile where the code.bin image is made - don't need my custom script | |||
==HowTo route between WLAN and LAN on a WRT54G with Sveasoft== | |||
Make sure you have installed Sveasoft Alchemy 5.2.4 | |||
Go to Administration - Diagnostics and enter the following into the command line | |||
brctl delif br0 eth1 | |||
ifconfig eth1 down | |||
ifconfig eth1 up | |||
if addr add 192.168.2.1/24 dev eth1 | |||
Click on "save startup" | |||
Reboot linksys | |||
This will create a new subnet for the wireless side of the router on the 192.168.2.0 network | |||
The LAN side of the router will remain on the 192.168.1.0 network | |||
==HowTo Cross compile for the WRT54G== | |||
Got a c++ program compiled for linksys | |||
The C++ environment is configured! | |||
*1. Download the linksys firmware source | |||
*2. Copy the brcm/ directory from /tools to /opt | |||
*3. add /opt/brcm/hndtools-mipsel-linux/bin to your path | |||
*4. add /opt/brcm/hndtools-mipsel-uclibc/bin to your path | |||
*Use mipsel-linux-g++ compiler to compile any c++ code | |||
*Don't use the mipsel-uclibc-g++ compiler - this was my mistake! | |||
*Now we can try compile mobile mesh for linksys | |||
=HowTo create/be part of a VPN= | =HowTo create/be part of a VPN= | ||
==Getting IPSEC installed on your Linksys using Freifunk== | |||
====Reflashing the firmware==== | |||
Follow the link to http://edna/ftp/pub/mesh/linksys/os/freifunk/firmware/openwrt-gl11-freifunk-1.2.5-de.bin | |||
Download this file and then upload to your router | |||
Login to the router via ssh | |||
Type the following commands | |||
ipkg update | |||
ipkg install libgmp | |||
ipkg install freifunk-openwrt-compat | |||
ipkg install openswan | |||
Now goto step 3 below to see how to configure IPSEC | |||
==Getting IPSEC installed on your Linksys using Openwrt (RC5)== | |||
===1. Upgrade Linksys to OpenWRT (RC5)=== | |||
There are two options: if one wants to upgrade to RC5 with all the required packages already built in, follow the instructions in (a). If RC5 is already installed and one needs to update the packages, follow the instructions in (b). | |||
====(a) Reflashing the firmware==== | |||
Tip: It migth be useful to copy the olsr.conf file from the Linksys to the host PC BEFORE upgrading. | |||
Follow the link ftp://ftp2.za.freebsd.org/pub/mesh/whiterussian_rc5/firmware/ to select the firmware (files with "-squashfs.bin") that matches the model of your LinkSys router. Note that a "new Linksys" implies a new Linksys used for the first time which has not been upgraded yet, i.e. the firmware that comes with Cisco - Linksys is installed. | |||
# Save the file on your client machine (machine connected to your LinkSys). | |||
# Logon via the web browser onto your LinkSys; e.g http://w.x.y.z ; where w.x.y.z is the ethernet address of your LinkSys (usually this is 192.168.1.1) | |||
# The system will/might ask (warn) you to set the password. Password must be set to change anything to the router. So, set password! Note after this step telnet will be disabled, and instead will need to use ssh instead "ssh root@w.x.y.z" | |||
#Upgrade the firmware: | |||
#*Openwrt: Select (under CATEGORIES) "System" then select "Firmware upgrade" | |||
#*New linksys: Select Administration; then select "Firmware Upgrade" | |||
# Choose to "Erase JFFS2 partition" under "Options" (Freifunk or new Linksys does not have this option) | |||
# Click on "Browse" to select the firmware you've downloaded from ftp://ftp2.za.freebsd.org | |||
# Click on "Upgrade" | |||
PLEASE DO NOT INTERRUPT THE UPGRADE PROCESS IN ANYWAY. Watch the DMZ light go on and then off after which time the router should be ready. Wait for about 3-5 minutes to be safe for the system to upgrade itself. | |||
When upgrading a new linksys, it will let display a new page on the web interface: "upgrade is successful". Pressing the Continue button will show: " The requested URL was not found on this server." This is because one has upgraded to OpenWRT which has a different URL. Point to the URL 192.168.1.1 again to see OpenWRT's web interface. | |||
====(b) Installing required packages==== | |||
If you have Openwrt(RC5) already installed but do not have IPSec then download from ftp://ftp2.za.freebsd.org/pub/mesh/whiterussian_rc5/packages/ the following packages and install them using ipkg in the order listed below: | |||
kmod-openswan_2.4.30brcm+2.4.4-2_mipsel.ipk | |||
libgmp_4.1.4-1_mipsel.ipk | |||
openswan_2.4.4-1_mipsel.ipk | |||
ip_2.6.11-050330-1_mipsel.ipk | |||
'''Below is what happens on my box:''' | |||
root@Lawrence:~# ipkg install kmod-openswan_2.4.30brcm\+2.4.4-2_mipsel.ipk | |||
Installing kmod-openswan (2.4.30brcm+2.4.4-2) to root... | |||
Configuring kmod-openswan | |||
Successfully terminated. | |||
root@Lawrence:~# ipkg install libgmp_4.1.4-1_mipsel.ipk | |||
Installing libgmp (4.1.4-1) to root... | |||
Configuring libgmp | |||
. | Successfully terminated. | ||
... | root@Lawrence:~# ipkg install openswan_2.4.4-1_mipsel.ipk | ||
.. | Installing openswan (2.4.4-1) to root... | ||
Configuring openswan | |||
. | Successfully terminated. | ||
... | root@Lawrence:~# ipkg install ip_2.6.11-050330-1_mipsel.ipk | ||
... | Installing ip (2.6.11-050330-1) to root... | ||
Configuring ip | |||
Successfully terminated. | |||
'''NOTE:''' | |||
It's important to note that although the 3 packages above are all the core packages for IPsec; IPsec might still not run depending on your current installation. For example, the script /etc/lib/ipsec/_updown, hence Ipsec, will fail to run if the command "ip" is not installed. | |||
===2. Configure network settings=== | |||
Configuration is done using the web interface. Unfortunately everything is not configurable via the web, and a second step of the configuration is required via an ssh session. | |||
'''Step 1: Configuration via web interface:''' | |||
*Click on Categories: Systen: Settings | |||
*enter new password (if it is the first time, it will ask for it) | |||
*login root, new passwd | |||
*Enter host name | |||
*Save settings | |||
*Click on Categories: Network: LAN | |||
*Enter Lan's IP address with the required netmask | |||
*Save Settings | |||
*Click on "WAN" | |||
*Select none | |||
*Save settings | |||
*click on "Wireless" | |||
*Select ESSID | |||
*Select Channel | |||
*select Mode: Ad-Hoc | |||
*Save settings | |||
*Apply changes | |||
*The linksys will reboot... | |||
'''Step 2: Configuration via ssh''' | |||
*ssh to root@192.168.1.1 | |||
*Remove Bridge | |||
nvram set lan_ifname=vlan0 | |||
nvram set lan_ifnames=vlan0 | |||
*Setup Wireless interface | |||
nvram set wifi_ifname=eth1 | |||
nvram set wifi_proto=static | |||
nvram set wifi_ipaddr=10.60.30.2 ##get ip address from your admin | |||
nvram set wifi_netmask=255.255.255.0 | |||
nvram commit | |||
nvram reboot | |||
* Setup olsr | |||
** copy olsrd.conf to Linksys's tmp dir | |||
**rm olsrd.conf in etc dir (breaking symbolic link to ROM) | |||
**copy olsr.conf ot the /etc dir | |||
**restart olsr or reboot | |||
*rm /etc/init.d/S45firewall | |||
===3. Configure IPSEC=== | |||
'''STOPPING IPSEC''' | |||
After the either of the above steps, ipsec will be run automatically. You need to stop IPSec before continuing with | |||
the follwoing steps. Do the following: | |||
ssh root@w.x.y.z | |||
root@LinkSys:/#ipsec setup stop | |||
CONFIGURATION | '''CONFIGURATION''' | ||
'''STEP 1:''' | |||
Do the following: | |||
# cd /etc | |||
# rm ipsec.conf #by default this file is created as a link to one found in /rom directory (which is read-only) | |||
# vi ipsec.conf #Edit by any means you can | |||
# Enter the following lines and save the file | |||
NOTE: You can ignore to type in the comments ( Text starting with/after #), however do as the comments say | |||
version 2 | |||
config setup | |||
interfaces="ipsec0=eth1" # replace "eth1" with the name of your wireless interface | |||
klipsdebug=none | |||
plutodebug=none | |||
uniqueids=yes | |||
conn %default | |||
keyingtries=0 | |||
authby=secret #rsasig | |||
conn crypt | |||
left=10.50.1.80 # replace "10.50.1.80" with the ip address of your wireless interface | |||
leftid=10.50.1.80 # replace "10.50.1.80" with the ip address of your wireless interface | |||
leftsubnet=10.1.13.1/24 # replace "10.1.13.1" with the ethernet ip address of your router | |||
right=10.50.1.3 # replace "10.50.1.3" with the ip address of the IPSec server. Ask Net admin | |||
rightid=10.50.1.3 # replace "10.50.1.3" with the ip address of the IPSec server. Ask Net admin | |||
rightsubnet=146.64.8.8/16 # Do not change this line to access CSIR network | |||
auto=start # This line ensures IPSec is automatically started when the router starts up. | |||
type=tunnel | |||
'''STEP 2:''' | |||
Edit the /etc/ipsec.secrets to contain a line similar to the one below in between the stars (excluding the stars) | |||
10.50.1.3 10.50.1.80: PSK "presharedkey" | |||
NOTE: The Ip addresses above should be as in ipsec.conf above. Ask the Net admin for the string pre-shared key (presharedkey) which | |||
must be enclosed in double quotes as shown above. | |||
'''RUNNING IPSEC''' | |||
root@LinkSys:/#ipsec setup restart | |||
'''TEST IPSEC''' | |||
At this point, you should be able to reach/ping any machine on the rightsubnet (146.64.X.Y as in the ipsec.conf above) as specified | |||
in your ipsec.conf file. | |||
==Establishing IPsec tunnel/connection between FreeBSD and Linux (openswan IPsec Cisco WRT54G Router)== | |||
Below is a simple setup demonstrating steps to establish an IPsec connection/tunnel between two machines one running Ipsec/racoon (on FreeBSD) and the other running openswan Ipsec (on WRT54G running Linux) using pre-shared key: This IPsec setup example shows how to control the Private LAN_A (146.64.0.0) network access. | |||
.........(INTERNET) | |||
.........| | |||
.........| | |||
..| FreeBSD | ......10.50.1.3..............................10.50.1.80| Openswan IPsec| | |||
.| Router_A |<========> (“NETWORK”)<=======>| Router_B | | |||
.| 146.64.17.1 |................................................................| 10.1.13.1 | | |||
............ ||.........................................................................|| | |||
...Private LAN_A....................................................PPrivate LAN_B | |||
...........|.......................................................................................|........... | |||
....Client_A (146.64.17.12) ..................................Client_B (10.1.13.130) | |||
NOTE: Before running racoon/ipsec and openswan ipsec, ensure that all nodes can successfully reach (ping) each other. | |||
INSTALLING OPENSWAN ON WRT54G | |||
To install, add the following to /etc/ipkg.conf: | |||
src openswan ftp://ftp.openswan.org/openswan/binaries/openwrt/buildroot-20040509/ipkg/ | |||
and then run: | |||
ipkg update | |||
ipkg install gmp mawk openswan-module openswan | |||
NOTE: Since /etc/ipkg.conf would normally be a link to the file in /rom directory; You can simple delete the link, and then copy the file over. | |||
CONFIGURATION (Router_A IPsec) | |||
There are three (3) configuration files on Router_A that needs to be edited: ipsec.conf (found in /etc on FreeBSD), psk.conf.(found in /usr/local/etc/racoon/ on FreeBSD) and racoon.conf.(found in /usr/local/etc/racoon/ on FreeBSD). | |||
Add the following two lines in ipsec.conf: (This file defines the ends points of the tunnel to be established. There’d be two lines for each LAN_B client ) | |||
spdadd 146.64.0.0/16 10.1.13.0/24 any -P out ipsec esp/tunnel/10.50.1.3-10.50.1.80/require; | |||
spdadd 10.1.13.0/24 146.64.0.0/16 any -P in ipsec esp/tunnel/10.50.1.80-10.50.1.3/require; | |||
Roughly; the first line says “traffic coming from 146.64.0.0 network destined for 10.1.13.0 network must be transported via an IPsec tunnel with local endpoint 10.50.1.3 and far endpoint 10.50.1.80”. | |||
The second line says “traffic coming from 10.1.13.0 network destined for 146.64.0.0 network must/would use an IPsec tunnel with a far endpoint 10.50.1.80 and local endpoint 10.50.1.3”. | |||
Add the following line to psk.conf (This file defines the pre-shared key to be used between Router_A and Router_B). | |||
10.50.1.80 presharedkey | |||
NOTE: Comments must be on a different line to the pre-shared key entry, otherwise the comments are interpreted as part of the pre-shared key. | |||
Add the following lines to racoon.conf | |||
path pre_shared_key "/usr/local/etc/racoon/psk.txt" ; | |||
remote anonymous | |||
{ | |||
# exchange_mode aggressive,main ; | |||
exchange_mode main ; | |||
lifetime time 24 hour ; | |||
proposal { | |||
encryption_algorithm 3des ; | |||
hash_algorithm sha1; | |||
authentication_method pre_shared_key ; | |||
dh_group 2 ; | |||
} | |||
} | |||
sainfo anonymous | |||
{ | |||
lifetime time 12 hour ; | |||
encryption_algorithm 3des, blowfish, des, rijndael ; | |||
authentication_algorithm hmac_sha1, hmac_md5 ; | |||
compression_algorithm deflate ; | |||
} | |||
IMPORTANT: The IPsec version (2.3.1) used in this example did not seem to support “aggressive” exchange_mode hence “main” is specified. However, it is possible to include more than mode by separating them with comma; i.e. | |||
exchange_mode aggressive, main ; | |||
Both ways (specifying one or more modes) works! Further other lines with more than one values separated by comma may contain only one value as described for exchange_mode above. | |||
CONFIGURATION (Openswan IPsec, Router_B) | |||
There are two (2) files on Router_B that needs editing: ipsec.conf (found in /etc on Linux) and ipsec.secrets (found in /etc on Linux). | |||
Add the following line in ipsec.secrets: (This file defines the ends points of the tunnel to be established and also the pre-shared key to be used) | |||
10.50.1.3 10.50.1.80: PSK “presharedkey” | |||
NOTE: 1. Place the string after PSK in quotes if it does not start with 0x (as in a hexadecimal number), otherwise openswan will complain. | |||
2. The string after PSK must be the same as that specified in psk.conf on Router_A. | |||
Add the following lines in ipsec.conf: (This file defines among other things, the network to be protected, authentication methods, type of connection, etc.) | |||
config setup | |||
interfaces="ipsec0=eth1" | |||
klipsdebug=none | |||
plutodebug=none | |||
uniqueids=yes | |||
conn %default | |||
keyingtries=0 | |||
authby=secret #rsasig | |||
conn crypt | |||
left=10.50.1.80 | |||
leftid=10.50.1.80 | |||
leftsubnet=10.1.13.1/24 | |||
right=10.50.1.3 | |||
rightid=10.50.1.3 | |||
rightsubnet=146.64.8.8/16 | |||
auto=start | |||
type=tunnel | |||
NOTE: The name of our connection is called “crypt”. Under “config setup”, the line interfaces=”ipsec0=eth1” must refer to a real interface (ifconfig will show available interfaces) and also must be the interface through which the data to be protected will travel, in case of more than one NIC. The line “auto=start” says, the connection “crypt” must be brought up when openswan ipsec starts up; to bring up the connection manually either comment out the line or specify “auto=ignore”. The explanation given for ipsec.conf on Router_A is pretty much the same as for Router_B. | |||
STARTING UP IPsec and Racoon (FreeBSD). | STARTING UP IPsec and Racoon (FreeBSD). | ||
| Line 801: | Line 1,200: | ||
Running this script will show the various key exchange messages. The messages are pretty much clear to see what it’s happening. | Running this script will show the various key exchange messages. The messages are pretty much clear to see what it’s happening. | ||
=HowTo stop DHCP client over-writing resolv.conf= | =HowTo stop DHCP client over-writing resolv.conf= | ||
| Line 813: | Line 1,210: | ||
Comment out the line that requests for domain-name, domain-name-servers and host-name | Comment out the line that requests for domain-name, domain-name-servers and host-name | ||
request subnet-mask, broadcast-address, time-offset, routers, | request subnet-mask, broadcast-address, time-offset, routers, | ||
# domain-name, domain-name-servers, host-name, | # domain-name, domain-name-servers, host-name, | ||
netbios-name-servers, netbios-scope; | netbios-name-servers, netbios-scope; | ||
=HowTo setup DHCP with OLSR= | =HowTo setup DHCP with OLSR= | ||
| Line 848: | Line 1,245: | ||
The subnet mask after the comma (255.255.255.240) is an alternative to the slash format /28. Why does everyone have this reduntant subnet mask on their postings??? | The subnet mask after the comma (255.255.255.240) is an alternative to the slash format /28. Why does everyone have this reduntant subnet mask on their postings??? | ||
=HowTo setup your own network profiles on a laptop= | =Linux HowTos= | ||
==HowTo setup your own network profiles on a laptop== | |||
I have always wanted to write some good scripts that configure my laptop for home and work wireless/ethernet automatically in ubuntu and so I set about building up a set of scripts that I can call. | I have always wanted to write some good scripts that configure my laptop for home and work wireless/ethernet automatically in ubuntu and so I set about building up a set of scripts that I can call. | ||
| Line 991: | Line 1,389: | ||
sudo ifup eth0 | sudo ifup eth0 | ||
==HowTo Setup a Linux machine to become an access point== | |||
1. Make sure you install dhcpd off the Mandrake disks | |||
2. Put the Wireless card into access point mode with the following example script /etc/sysconfig/network-scripts/ifcfg-wifi0 | |||
DEVICE=wifi0 | |||
BOOTPROTO=static | |||
IPADDR=192.168.0.1 | |||
ONBOOT=yes | |||
NETMASK=255.255.255.0 | |||
NETWORK=192.168.0.0 | |||
BROADCAST=192.168.0.255 | |||
DHCP_TIMEOUT=5 | |||
WIRELESS_MODE=Master | |||
WIRELESS_ESSID=mesh | |||
WIRELESS_CHANNEL=10 | |||
3. run ifup wifi0 | |||
4. copy /etc/dhcpd.conf.sample (this file only exisits the first time you install dhcpd) to dhcpd.conf ... Change the IP address allocations in this file to suite your needs | |||
5. start dhcpd with /etc/rc.d/init.d/dhcpd | |||
6. Check the /var/lib/dhcpd/dhcpd.leases to check which IP addresses are being assigned | |||
==HowTo Set up the SENOA card in linux== | |||
1. Download the hostap driver from ftp://edna.icomtek.csir.co.za/pub/drivers ... This driver ensures that the SENOA card can run in Access point mode as well as Ad-Hoc and Infrastructure | |||
2. Unzip using gunzip < hostap-driver-0.2.4.tar.gz | tar xvf - | |||
3. Change Makefile to include KERNEL_PATH ... KERNEL_PATH=/usr/src/linux | |||
4. Run 'make' | |||
5. run 'make install' | |||
6. Restart card manager using /etc/rc.d/init.d/pcmcia restart | |||
If you are using the PCI to PCMCIA bridge card with the RLSC475 chipset follow these steps | |||
1. Edit the file /etc/sysconfig/pcmcia to include these lines | |||
PCMCIA=yes | |||
PCIC=RLSC475 | |||
2. Run /etc/rc.d/init.d/pcmcia restart | |||
==Linux network configurations tips== | |||
1. Setting IP address and modes of interface | |||
The file /etc/sysconfig/network-scripts/ifcfg-eth0 contains all the settingsfor interface eth0 including | |||
IP allocation type (static or dynamic) | |||
IP Address | |||
Subnet mask | |||
Broadcast address | |||
Wireless mode | |||
wireless channel | |||
type | |||
# man ifcfg | |||
to see all the options for this config file | |||
Use | |||
# ifup eth0 | |||
to bring eth0 network interface up using the script ifcfg-eth0 | |||
#ifdown eth0 | |||
to pull the eth0 interface down | |||
2. The DNS nameserver | |||
The file /etc/resolve.conf contains the nameserver (dns) to use for the network | |||
3. The gateway and other network routes | |||
To see the current network routes type | |||
# route | |||
This will show you all the routes which the network is currently using | |||
To add a new route for interface eth0 type | |||
# route add -net 10.0.0.0 netmask 255.255.255.0 dev eth0 | |||
This adds a route to the network 10.0.0.0 using device eth0 | |||
# route add default gw 10.0.0.8 | |||
Adds a default route which will be used if no other route matches. | |||
There should be an existing route, in this case, to 10.0.0.8 through some interface. | |||
=HowTo use the freespace loss equation= | |||
From: [http://www.swisswireless.org/wlan_calc_en.html Radio theory and link planning for Wireless LAN (WLAN)] | |||
Everyone should know the free space loss equation in their head | |||
Loss [ dB] = 32.44 + 20(Log(distance[km]) + Log(freq[MHz])) | |||
Useful cable losses | |||
RG58 = 1 dB/m | |||
RG213 = -.6 dB/m | |||
RG174 = 2 dB/m (often used in pigtails) | |||
LMR-400 = 0.22 dB/m | |||
Typical WiFi sensitivity for orinoco cards | |||
11Mbps = -82dBm | |||
5.5Mbps = -87dBm | |||
2Mbps = -92dBm | |||
1Mbps = -94dBm | |||
Typical allowed signal to noise ratios for orinoco cards | |||
11Mbps = 16dB | |||
5.5Mbps = 11dB | |||
2Mbps = 7dB | |||
1Mbps = 4dB | |||
Typical Noise level at 2.4GHz = -100dBm. Compute S/N level eg. at 11Mbps = -84dBm but sensitivity is -82dBm so sensitivity is the limiting factor. | |||
Just worked out that with our 2 8dBi omnis, 2dB loss in the RF cable each side of the link and the 200mW SENOA cards it is possible to acheive a theoretical distance of 5km with a 3dB margin (margin probably a bit tight), 4km will give you a 5dB margin - probably more realistic. | |||
Latest revision as of 14:42, 1 October 2006
Getting started
NEW! The first edition of "Wireless Networking in the Deveolping World" is available as e-book now. Prints can be ordered on demand at lulu.com. The e-book is available at no cost under a creative commons license. Get your copy at wndw or locally and share it.
Step 1. Check where you are on the planet:
Your very first step is to find your current position on a map and then see what other wireless nodes are nearby. The best way to do this is to get a GPS and find out your coordinates and then to enter these into google earth - you can also use google earth to find your coordinates by identifying your house on the satellite image.
Step 2. Check who else is around that you can connect to
Once you have entered your google earth position - have a look at the positions of other wifi installations around you. For the Pretoria Mesh we have stored all the google earth positions in this file. You can also have a look on sites like NodeDB to see if there are other wireless installations near you. Once you have identified someone that you want to connect to, the best way to check connectivity is to use a WiFi sniffer such as netsumbler for windows or Kismet on linux loaded on a laptop with a Wifi card fitted with an external antenna. For people in Pretoria we have a kit like this that can be borrowed from our WiFi tuckshop. Find the highest point at your house such as your roof and slowly rotate the directional antenna around you to see if you can pick up any WiFi access points. You will want to find an access point that is in ad-hoc mode and is mesh enabled - the wifi sniffer will tell you if the wireless node is in ad-hoc mode but you will have to contact the owner to check what mesh protocol, if any, they are running.
Step 3. Build a mesh node
Now that you know where you are located and you have hopefully found someone you can connect to, you will need to construct your mesh hardware.
A mesh network node consists of a wireless router, antenna, routing software and settings.
Wireless Router
Your wireless router can either be a PC with a wireless card, a dedicated Wireless Router unit or SBC Single Board Computer with a wireless card. A dedicated Wireless Router is the most popular choice because it is relatively cheap, easy to configure and low power making it practicle for a device that is meant to be on most of the time. Have a look at Cost Tables to get an idea of all the possible types of mesh nodes you can build together with the cost implications
Antennae:
The first step is to select an antenna that suits your situation best. There are several types of Antennae:
1) Omnidirectional 2) Yagi-Uda 3) Grid 4) Flat-panel 5) Wave-guide
The main difference between these antennae is the Radiation Pattern. Each type is also available with different Gain specifications. Typical Wireless Routers are sold with 2 omnidirectional antennae and these can be re-used as part of your node, depending on your situation. If you have other nodes in your vicinity that are spread out in all directions but are fairly close (i.e. < 3Km), then an omni-directional antenna should suffice. If the other nodes are concentrated in one direction, for example, if you have a hill on one side of your house and theres no point in radiating the hill, then you may want to choose a more directional antenna, like a 180 degree Flat-panel. For point-to-point links, a smaller radiation angle is needed and Grid or Yagi-Uda type antennae are probably best suited.
Step 4. Install latest mesh networking firmware
The type of software that needs to be installed will typically be implmentations of mesh routing protocols like OLSR, as well as security software, like VPN clients. On dedicated wireless routers, this is typically implemented on Firmware, while on standard PC's its implemented in Software.
WRT54G Firmware update
Wireless Routers like the WRT54G are not mesh capable as is. One of the reasons for selecting the Linksys is that the Firmware is upgradeable.
Caution: Please note, that fiddling with the firmware will void your warranty!!!
The following instructions apply to networks running the OLSR routing protocl, like the Pretoria Mesh.
1. Download freifunk firmware from Freifunk site or Local
2. Set boot wait on linksys
Web method:
Navigate to web page were you can send pings and type each of these lines one line at a time
;cp${IFS}*/*/nvram${IFS}/tmp/n
;*/n${IFS}set${IFS}boot_wait=on
;*/n${IFS}commit
;*/n${IFS}show>tmp/ping.log
NVRAM method:
telnet into box and type the following
nvram set boot_wait=on nvram commit reboot
3. Upload firmware
Give yourself a fixed IP in the 192.168.1.x range e.g. 192.168.1.100
Use tftp to upload firmware
tftp 192.168.1.1 tftp> binary tftp> rexmt 1 tftp> trace Packet tracing on. tftp> put openwrt-g-freifunk-1.0.2-en.bin
Wait for the power light to stop flashing Power cycle the box
Step 5. Install mesh node
HowTo Water-proof your equipment
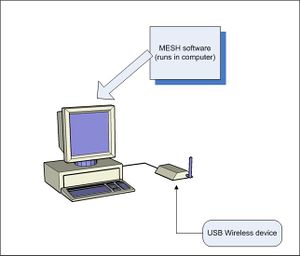
Step 6. Setup mesh configuration
1. Check that the web interface is working. Visit the site http://192.168.1.1 on your web browser - you should see the main freifunk web interface appear
2. Set up the wireless interface
WLAN protocol: Static Ip Address: 192.168.2.5 Netmask: 255.255.255.0 WLAN Mode: Ad Hoc (Peer to Peer) ESSID: mesh Channel: 6 TX Power: 100
3. Set up the LAN interface
LAN protocol: Static LAN IP: 192.168.4.1 LAN Netmask: 255.255.255.0 Disable NAT: yes Disable Firewall: yes
4. Set up the WAN interface
WAN Protocol: DHCP Host name: Lawrence
5. Set up OLSR
HNA4: 192.168.4.1 255.255.255.0
6. Restart the Linksys
You should now be given an IP address in the 192.168.3.x range You should be able to connect to another mesh access point and even get a default gateway to an internet point, if one exists
Step 7. Start surfing
Hopefully you`re now hooked up to the internet and you can start surfing the web or hooking up to other PCś on the mesh
Step 8. Troubleshoot
Start with Layer 1:
Is everything switched on? Is the LAN plugged in? Is the Antenna connected? Is it facing the right direction? Is it polarised correctly?
Check software settings:
Is the correct antenna selected? Is the routing daemon running?
WRT54G HowTos
HowTo choose which antenna port to use on the WRT54G for an external antenna
Where to connect the external antenna
WRT54g v1, v1.1, v2 look at the backside and connect the external antenna to the right antenna connector
WRT54g v2.2 v3 3.1 v4 and the WRT54GL v1.0 look at the backside and connect the external antenna to the left antenna connector
HowTo create an ipk package
TOOLS
Get the script rightfully called ipkg-build at, among other places, ftp://ftp.handhelds.org/packages/ipkg-utils, or http://www.mizi.com/download/mz20/ipkg-build.
CREATING THE PACKAGE STRUCTURE
Say you wanna create a package called MyPackage; you further wanna package the project called MyProject. Then do the following:
1. Create a directory called MyPackage. 2. Inside directory MyPackage, create a directory called CONTROL. 3. Copy your project (MyProject) to the MyPackage directory. 4. Inside directory CONTORL creating a file called control.
NOTE:
When the package is installed on the target, the MyPAckage directory will be created with respect to root. So if you wanted your files to be installed in /usr/bin on the target system, then our project would in this case be “/usr/bin”. That is you create inside directory MyPackage a directory called /usr/bin.
FORMAT AND CONTENTS OF /CONTROL/control
Package: MyPackage
Priority: optional // default
Version: 1.0 //package version
Architecture: mipsel
Maintainer: I_maintain@you.com
Source: ftp:ftp:122.122.122.122 //See Note below
Section: misc //See Note below
Description: This is an attempt to create ipkg.
NOTE:
The fields Section and Source seem rather useless to me in this example and I initially left them out; however the ipkg-build script complained requiring them, so I just put them in as a workaround without knowing/”caring” of their need. There are other fields not included here which you might need for your purposes, check the web for more.
Further the comments are mine for this documentation purposes only and the script MIGHT NOT permit comments.
RUNNING THE ipkg-build SCRIPT
Now simply run (of course being outside of the directory MyPackage):
“./ipkg-build –c –o root –g root MyPackage” // as root or non-root, or
“./ipkg-build –c MyPackage” //as root
IF all’s well, a package on the current directory will be created.
NOTE:
Without the “-c” option, I could not get the package installed successfully, you can try with or without and see for yourself.
HowTo run Kismet on a WRT54G
- Install either the kismet or kismet_drone package.
- Edit /etc/kismet_drone.conf and change the source from wrt54g,eth1,wrt45g to wrt54g,prism0,wrt54g.
- Run kismet from your host, pc and off u go!
HowTo check your Linksys WRT54G version
Finally some good info about finding the version number from outside markings and using NVRAM settings - info from www.openwrt.org
Linksys WRT54G
1. Hardware versions
1. Identification by S/N
1. WRT54G v1.0
2. WRT54G v1.1
3. WRT54G v2.0
4. WRT54G v2.2
5. WRT54G v3.0 & WRT54G v3.1
6. WRT54G v4.00
2. Table summary
3. Hardware hacking
1. Hardware versions
There are currently seven versions of the WRT54G (v1.0, v1.1, v2.0, v2.2, v3.0, v3.1, v4.00). With the exception of v4.00 devices (it is currently marked as untested for White Russian RC1), the WRT54G units are supported by OpenWrt 1.0 (White Russian) and later. boot_wait is off by default on these routers, so you should turn it on. The version number is found on the label on the bottom of the front part of the case below the Linksys logo. 1.0.1. Identification by S/N
Useful for identifying shrinkwrapped units. The S/N can be found on the box, below the UPC barcode.
(!) Please contribute to this list. (!)
| Model | S/N | CVS | EXP |
| WRT54G v1.1 | CDF20xxxxxxx CDF30xxxxxxx | (./) | (./) |
| WRT54G v2 | CDF50xxxxxxx | (./) | (./) |
| WRT54G v2.2 | CDF70xxxxxxx | {X} | (./) |
| WRT54G v3 | CDF80xxxxxxx | {X} | (./) |
| WRT54G v3.1 (AU?) | CDF90xxxxxxx | {X} | (./) |
1.1. WRT54G v1.0
The WRT54G v1.0 is based on the Broadcom 4710 board. It has a 125MHz CPU, 4Mb flash and 16Mb SDRAM. The wireless NIC is a mini-PCI card. The switch is an ADM6996. 1.2. WRT54G v1.1
The WRT54G v1.1 is based on the Broadcom 4710 board. It has a 125MHz CPU, 4Mb flash and 16Mb SDRAM. The wireless NIC is soldered to the board. The switch is an ADM6996.
Hardware informations (nvram) :
boardtype=bcm94710dev
1.3. WRT54G v2.0
The WRT54G v2.0 is based on the Broadcom 4712 board. It has a 200MHz CPU, 4Mb flash and 16Mb SDRAM. The wireless NIC is integrated to the board. The switch is an ADM6996.
Hardware informations (nvram) :
boardtype=0x0101 boardflags=0x0188
1.4. WRT54G v2.2
The WRT54G v2.2 is based on the Broadcom 4712 board. It has a 200MHz CPU, 4Mb flash and 16Mb DDR-SDRAM. The wireless NIC is integrated to the board. The switch is a BCM5325.
Hardware informations (nvram) :
boardtype=0x0708 boardflags=0x0118
1.5. WRT54G v3.0 & WRT54G v3.1
This unit is just like the V2.2 Except it has an extra reboot button on the left front panel behind a Cisco logo. 1.6. WRT54G v4.00
Please add information for this revision.
Hardware informations (nvram) :
boardrev=0x10 boardtype=0x0708 boardflags2=0 boardflags=0x0118 boardnum=42
/!\ To take the front cover off of this unit you must first remove the small screws under the rubber covers of the front feet! 2. Table summary
how to get info :
- board info: nvram show | grep board | sort
- cpu model: cat /proc/cpuinfo | grep cpu
| Model | boardrev | boardtype | boardflags | boardflags2 | boardnum | wl0_corerev | cpu model |
| WRT54G v1.1 | bcm94710dev | 42 | 5 | BCM4710 V0.0 | |||
| WRT54G v2.0 | 0x0101 | 0x0188 | BCM3302 V0.7 | ||||
| WRT54G v2.2 | 0x0708 | 0x0118 | 7 | ||||
| WRT54G v3.0 | 0x10 | 0x0708 | 0x0118 | 0 | 42 | 7 | BCM3302 V0.7 |
| WRT54G v3.1 (AU?) | 0x10 | 0x0708 | 0x0118 | 0 | 42 | 7 | BCM3302 V0.7 |
| WRT54G v4.0 | 0x10 | 0x0708 | 0x0118 | 0 | 42 | 7 | BCM3302 V0.7 |
| WRT54GS v1.0 | 0x10 | 0x0101 | 0x0388 | 0 | 42 | 7 | BCM3302 V0.7 |
| WRT54GS v1.1 | 0x10 | 0x0708 | 0x0318 | 0 | 42 | ||
| Buffalo WBR-54G | 0x10 | bcm94710ap | 0x0188 | 2 | 42 | ||
| Toshiba WRC1000 | bcm94710r4 | 100 | |||||
| Buffalo WBR2-G54S | 0x10 | 0x0101 | 0x0188 | 0 | 00 | ||
| Asus WL-500G Deluxe | 0x10 | bcm95365r | 45 | 5 | BCM3302 V0.7 |
- other variables (nvram) of interest : boot_ver, pmon_ver, firmware_version, os_version
please complete this table. Look at this thread : [WWW] http://openwrt.org/forum/viewtopic.php?pid=8127#p8127 May be this table should move up to OpenWrtDocs/Hardware. 3. Hardware hacking
There are revision XH units of the WRT54G v2.0. These units have 32Mb of memory, but they are locked to 16Mb. You can unlock the remaining memory with changing some of the variables. Afterburner (aka. Speedbooster) mode can be enabled with some variables, too.
/!\ However, there are no guaranties, that these will work, and changing the memory configuration on a non-XH unit will give You a brick. Check the forums for more info. If you have a look at the WRT54G v2.2 board, you can find on the left corner, near the power LED, an empty place for a 4 pins button. On the board it is printed as SW2. This is the second reset button you can find on WRT54G v3.0, except that it has not been soldered.
HowTo Stabilise a ver 2.2 WRT54G running OpenWRT based firmware
After a lot of tweaking OLSR running on Linksys has had no "ping down" messages for about 5 days now. Some of the tips to getting OLSR on OpenWRT stable.
1. Lock all the nodes to 802.11B don't let it auto sense 2. If there are any v2.2 hardware devices, change the clock speed to 216MHz with the following commands1
- nvram set clkfreq=216
- nvram commit
- reboot
3. Lock the RX and TX antenna to the one you connected your external antenna too, don't use AUTO. TAKE NOTE!!! On Version 2.0 hardware Antenna A is on the left looking from the front of the linksys and and on Version 2.,2 hardware Antenna A is on the right looking from the fron of the linksys. This caught me out a few times.
HowTo configure netmasks on OLSR/Freifunk
I had this problem with the OLSR web interface on the Freifunk openwrt implementation. If entered the following for the HNA4 field
HNA4: 10.3.13.1 255.255.255.0
Which should advertise the whole 10.3.13.x net it would advertise the 10.0.0.0 net. I discovered that it needs the subnet mask in this format instead
HNA4: 10.3.13.1/24
A few other things I learnt
1. NVRAM variable ff_hna4 stores the HNA4 setting 2. /etc/olsr.conf is ignored by freifunk 3. /rom/etc/olsrd.conf stores a permanent copy of the olsrd setup 4. /var/etc/olsrd.conf is a symbolic link to /tmp/etc/olsrd.conf ... this file is copied from /rom/etc/olsrd.conf into RAM (ramfs filesystem) and is the one called by olsrd.
ps -A will reveal that olsrd is called as follows
olsrd -f /var/etc/olsrd.conf -d 0
HowTo Brick and De-Brick a WRT54G
Theres nothing like learning the hard way! As a result of my usual "If it ain't broke, it hasn't been fixed enough" approach to life, I fiddled with the Linksys until it innevitably went into a coma/ vegetative state. How did I manage this you ask? Simple, I started by doing a firmware upgrade using the wrong sveasoft image, which resulted in a moderately upset linksys which refused to talk to me on the web interface. With the help of our trusted Android (Andrew), I managed to do a reset-hold/ ping / tftp recovery and then flashed the poor bugger with OpenWRT, which according to OpenWRT is still not supported by them for the version 2.2 Linksys, which I subsequently found out I was using! So alas, all that remained was a perfectly dead Linksys, not responding to anything. It was time to go in, screwdrivers a blazing. I shorted out pins 15 and 16 and started up the Linksys, this created a crc error which was detected on boot, this then started up an emergency TFTP server which allowed me to ping and finally tftp the original Linksys firmware back onto it!
More details on the recovery processes can be found here: OpenWrtDocs/Troubleshooting - OpenWrt
Whew!
How to set up Linksys as a RIP2 router with client mode
How to set up Linksys as a RIP2 router with client mode
1. Load Alchemy pre-release 5.2.3 onto the linksys
2. Set the Linksys Wireless interface to Client mode and set SSID to "pta-mesh"
Using the web interface select Wireless - Basic Settings Wireless Mode : Client SSID: pta-mesh Select Save Settings - continue
3. Choose your IP addresses for the Wireless interface and the LAN interface
I chose the following WAN interface: 10.50.1.13 LAN interface: 10.3.11.1
Using the Web interface select Setup - Basic Setup Internet Connection Type: Static IP Internet IP Address: 10.50.1.13 Subnet Mask: 255.255.255.0 Router Name: Something you like eg. david_home Local IP Address: 10.3.11.1 Subnet Mask: 255.255.255.0
Select Save Settings - continue
4. Add router configuration files to the target directory
Enter the router directory ($LINKSYS/src/router)
- cd /mipsel-uclibc/target
- mkdir /usr/local
- mkdir /usr/local/etc
Download my RIP configuration files for linksys ripd.conf zebra.conf
Copy these files to $LINKSYS/src/router/mipsel-uclibc/target/usr/local/etc
Download my image making script which will build files in the code.bin image makeimage.sh
Copy this script to $LINKSYS/src/router Run the script ./makeimage.sh
You should now have a code.bin with the router config files in /usr/local/etc Upload this new firmware to the linksys
5. Add commands to rc_startup to startup RIP, Flush iptables (so that RIP messages can arrive on RIP port) and remove NAT
zebra -d -f /usr/local/etc/zebra.conf ripd -d -f /usr/local/etc/ripd.conf iptables -F iptables -F -t nat
8. You should now have a rip enabled linksys client - Try ping the network connected to the wireless interface from a machine connected to the LAN
Things to improve in this recipe
1. Don't flush all iptables - just enable the port for RIP routing
2. Find location in Makefile where the code.bin image is made - don't need my custom script
HowTo route between WLAN and LAN on a WRT54G with Sveasoft
Make sure you have installed Sveasoft Alchemy 5.2.4
Go to Administration - Diagnostics and enter the following into the command line
brctl delif br0 eth1 ifconfig eth1 down ifconfig eth1 up if addr add 192.168.2.1/24 dev eth1
Click on "save startup" Reboot linksys
This will create a new subnet for the wireless side of the router on the 192.168.2.0 network The LAN side of the router will remain on the 192.168.1.0 network
HowTo Cross compile for the WRT54G
Got a c++ program compiled for linksys
The C++ environment is configured!
- 1. Download the linksys firmware source
- 2. Copy the brcm/ directory from /tools to /opt
- 3. add /opt/brcm/hndtools-mipsel-linux/bin to your path
- 4. add /opt/brcm/hndtools-mipsel-uclibc/bin to your path
- Use mipsel-linux-g++ compiler to compile any c++ code
- Don't use the mipsel-uclibc-g++ compiler - this was my mistake!
- Now we can try compile mobile mesh for linksys
HowTo create/be part of a VPN
Getting IPSEC installed on your Linksys using Freifunk
Reflashing the firmware
Follow the link to http://edna/ftp/pub/mesh/linksys/os/freifunk/firmware/openwrt-gl11-freifunk-1.2.5-de.bin Download this file and then upload to your router
Login to the router via ssh
Type the following commands
ipkg update ipkg install libgmp ipkg install freifunk-openwrt-compat ipkg install openswan
Now goto step 3 below to see how to configure IPSEC
Getting IPSEC installed on your Linksys using Openwrt (RC5)
1. Upgrade Linksys to OpenWRT (RC5)
There are two options: if one wants to upgrade to RC5 with all the required packages already built in, follow the instructions in (a). If RC5 is already installed and one needs to update the packages, follow the instructions in (b).
(a) Reflashing the firmware
Tip: It migth be useful to copy the olsr.conf file from the Linksys to the host PC BEFORE upgrading.
Follow the link ftp://ftp2.za.freebsd.org/pub/mesh/whiterussian_rc5/firmware/ to select the firmware (files with "-squashfs.bin") that matches the model of your LinkSys router. Note that a "new Linksys" implies a new Linksys used for the first time which has not been upgraded yet, i.e. the firmware that comes with Cisco - Linksys is installed.
- Save the file on your client machine (machine connected to your LinkSys).
- Logon via the web browser onto your LinkSys; e.g http://w.x.y.z ; where w.x.y.z is the ethernet address of your LinkSys (usually this is 192.168.1.1)
- The system will/might ask (warn) you to set the password. Password must be set to change anything to the router. So, set password! Note after this step telnet will be disabled, and instead will need to use ssh instead "ssh root@w.x.y.z"
- Upgrade the firmware:
- Openwrt: Select (under CATEGORIES) "System" then select "Firmware upgrade"
- New linksys: Select Administration; then select "Firmware Upgrade"
- Choose to "Erase JFFS2 partition" under "Options" (Freifunk or new Linksys does not have this option)
- Click on "Browse" to select the firmware you've downloaded from ftp://ftp2.za.freebsd.org
- Click on "Upgrade"
PLEASE DO NOT INTERRUPT THE UPGRADE PROCESS IN ANYWAY. Watch the DMZ light go on and then off after which time the router should be ready. Wait for about 3-5 minutes to be safe for the system to upgrade itself.
When upgrading a new linksys, it will let display a new page on the web interface: "upgrade is successful". Pressing the Continue button will show: " The requested URL was not found on this server." This is because one has upgraded to OpenWRT which has a different URL. Point to the URL 192.168.1.1 again to see OpenWRT's web interface.
(b) Installing required packages
If you have Openwrt(RC5) already installed but do not have IPSec then download from ftp://ftp2.za.freebsd.org/pub/mesh/whiterussian_rc5/packages/ the following packages and install them using ipkg in the order listed below:
kmod-openswan_2.4.30brcm+2.4.4-2_mipsel.ipk
libgmp_4.1.4-1_mipsel.ipk
openswan_2.4.4-1_mipsel.ipk
ip_2.6.11-050330-1_mipsel.ipk
Below is what happens on my box:
root@Lawrence:~# ipkg install kmod-openswan_2.4.30brcm\+2.4.4-2_mipsel.ipk
Installing kmod-openswan (2.4.30brcm+2.4.4-2) to root...
Configuring kmod-openswan
Successfully terminated.
root@Lawrence:~# ipkg install libgmp_4.1.4-1_mipsel.ipk
Installing libgmp (4.1.4-1) to root...
Configuring libgmp
Successfully terminated.
root@Lawrence:~# ipkg install openswan_2.4.4-1_mipsel.ipk
Installing openswan (2.4.4-1) to root...
Configuring openswan
Successfully terminated.
root@Lawrence:~# ipkg install ip_2.6.11-050330-1_mipsel.ipk
Installing ip (2.6.11-050330-1) to root...
Configuring ip
Successfully terminated.
NOTE: It's important to note that although the 3 packages above are all the core packages for IPsec; IPsec might still not run depending on your current installation. For example, the script /etc/lib/ipsec/_updown, hence Ipsec, will fail to run if the command "ip" is not installed.
2. Configure network settings
Configuration is done using the web interface. Unfortunately everything is not configurable via the web, and a second step of the configuration is required via an ssh session.
Step 1: Configuration via web interface:
- Click on Categories: Systen: Settings
- enter new password (if it is the first time, it will ask for it)
- login root, new passwd
- Enter host name
- Save settings
- Click on Categories: Network: LAN
- Enter Lan's IP address with the required netmask
- Save Settings
- Click on "WAN"
- Select none
- Save settings
- click on "Wireless"
- Select ESSID
- Select Channel
- select Mode: Ad-Hoc
- Save settings
- Apply changes
- The linksys will reboot...
Step 2: Configuration via ssh
- ssh to root@192.168.1.1
- Remove Bridge
nvram set lan_ifname=vlan0 nvram set lan_ifnames=vlan0
- Setup Wireless interface
nvram set wifi_ifname=eth1 nvram set wifi_proto=static nvram set wifi_ipaddr=10.60.30.2 ##get ip address from your admin nvram set wifi_netmask=255.255.255.0 nvram commit nvram reboot
- Setup olsr
- copy olsrd.conf to Linksys's tmp dir
- rm olsrd.conf in etc dir (breaking symbolic link to ROM)
- copy olsr.conf ot the /etc dir
- restart olsr or reboot
- rm /etc/init.d/S45firewall
3. Configure IPSEC
STOPPING IPSEC
After the either of the above steps, ipsec will be run automatically. You need to stop IPSec before continuing with the follwoing steps. Do the following:
ssh root@w.x.y.z
root@LinkSys:/#ipsec setup stop
CONFIGURATION
STEP 1:
Do the following:
- cd /etc
- rm ipsec.conf #by default this file is created as a link to one found in /rom directory (which is read-only)
- vi ipsec.conf #Edit by any means you can
- Enter the following lines and save the file
NOTE: You can ignore to type in the comments ( Text starting with/after #), however do as the comments say
version 2 config setup interfaces="ipsec0=eth1" # replace "eth1" with the name of your wireless interface klipsdebug=none plutodebug=none uniqueids=yes conn %default keyingtries=0 authby=secret #rsasig conn crypt left=10.50.1.80 # replace "10.50.1.80" with the ip address of your wireless interface leftid=10.50.1.80 # replace "10.50.1.80" with the ip address of your wireless interface leftsubnet=10.1.13.1/24 # replace "10.1.13.1" with the ethernet ip address of your router right=10.50.1.3 # replace "10.50.1.3" with the ip address of the IPSec server. Ask Net admin rightid=10.50.1.3 # replace "10.50.1.3" with the ip address of the IPSec server. Ask Net admin rightsubnet=146.64.8.8/16 # Do not change this line to access CSIR network auto=start # This line ensures IPSec is automatically started when the router starts up. type=tunnel
STEP 2:
Edit the /etc/ipsec.secrets to contain a line similar to the one below in between the stars (excluding the stars)
10.50.1.3 10.50.1.80: PSK "presharedkey"
NOTE: The Ip addresses above should be as in ipsec.conf above. Ask the Net admin for the string pre-shared key (presharedkey) which must be enclosed in double quotes as shown above.
RUNNING IPSEC
root@LinkSys:/#ipsec setup restart
TEST IPSEC
At this point, you should be able to reach/ping any machine on the rightsubnet (146.64.X.Y as in the ipsec.conf above) as specified
in your ipsec.conf file.
Establishing IPsec tunnel/connection between FreeBSD and Linux (openswan IPsec Cisco WRT54G Router)
Below is a simple setup demonstrating steps to establish an IPsec connection/tunnel between two machines one running Ipsec/racoon (on FreeBSD) and the other running openswan Ipsec (on WRT54G running Linux) using pre-shared key: This IPsec setup example shows how to control the Private LAN_A (146.64.0.0) network access.
.........(INTERNET)
.........|
.........|
..| FreeBSD | ......10.50.1.3..............................10.50.1.80| Openswan IPsec|
.| Router_A |<========> (“NETWORK”)<=======>| Router_B |
.| 146.64.17.1 |................................................................| 10.1.13.1 |
............ ||.........................................................................||
...Private LAN_A....................................................PPrivate LAN_B
...........|.......................................................................................|........... ....Client_A (146.64.17.12) ..................................Client_B (10.1.13.130)
NOTE: Before running racoon/ipsec and openswan ipsec, ensure that all nodes can successfully reach (ping) each other.
INSTALLING OPENSWAN ON WRT54G
To install, add the following to /etc/ipkg.conf:
src openswan ftp://ftp.openswan.org/openswan/binaries/openwrt/buildroot-20040509/ipkg/
and then run:
ipkg update
ipkg install gmp mawk openswan-module openswan
NOTE: Since /etc/ipkg.conf would normally be a link to the file in /rom directory; You can simple delete the link, and then copy the file over.
CONFIGURATION (Router_A IPsec)
There are three (3) configuration files on Router_A that needs to be edited: ipsec.conf (found in /etc on FreeBSD), psk.conf.(found in /usr/local/etc/racoon/ on FreeBSD) and racoon.conf.(found in /usr/local/etc/racoon/ on FreeBSD).
Add the following two lines in ipsec.conf: (This file defines the ends points of the tunnel to be established. There’d be two lines for each LAN_B client )
spdadd 146.64.0.0/16 10.1.13.0/24 any -P out ipsec esp/tunnel/10.50.1.3-10.50.1.80/require; spdadd 10.1.13.0/24 146.64.0.0/16 any -P in ipsec esp/tunnel/10.50.1.80-10.50.1.3/require;
Roughly; the first line says “traffic coming from 146.64.0.0 network destined for 10.1.13.0 network must be transported via an IPsec tunnel with local endpoint 10.50.1.3 and far endpoint 10.50.1.80”.
The second line says “traffic coming from 10.1.13.0 network destined for 146.64.0.0 network must/would use an IPsec tunnel with a far endpoint 10.50.1.80 and local endpoint 10.50.1.3”.
Add the following line to psk.conf (This file defines the pre-shared key to be used between Router_A and Router_B).
10.50.1.80 presharedkey
NOTE: Comments must be on a different line to the pre-shared key entry, otherwise the comments are interpreted as part of the pre-shared key.
Add the following lines to racoon.conf
path pre_shared_key "/usr/local/etc/racoon/psk.txt" ;
remote anonymous
{
# exchange_mode aggressive,main ;
exchange_mode main ;
lifetime time 24 hour ;
proposal {
encryption_algorithm 3des ;
hash_algorithm sha1;
authentication_method pre_shared_key ;
dh_group 2 ;
}
}
sainfo anonymous
{
lifetime time 12 hour ;
encryption_algorithm 3des, blowfish, des, rijndael ;
authentication_algorithm hmac_sha1, hmac_md5 ;
compression_algorithm deflate ;
}
IMPORTANT: The IPsec version (2.3.1) used in this example did not seem to support “aggressive” exchange_mode hence “main” is specified. However, it is possible to include more than mode by separating them with comma; i.e.
exchange_mode aggressive, main ;
Both ways (specifying one or more modes) works! Further other lines with more than one values separated by comma may contain only one value as described for exchange_mode above.
CONFIGURATION (Openswan IPsec, Router_B)
There are two (2) files on Router_B that needs editing: ipsec.conf (found in /etc on Linux) and ipsec.secrets (found in /etc on Linux).
Add the following line in ipsec.secrets: (This file defines the ends points of the tunnel to be established and also the pre-shared key to be used)
10.50.1.3 10.50.1.80: PSK “presharedkey”
NOTE: 1. Place the string after PSK in quotes if it does not start with 0x (as in a hexadecimal number), otherwise openswan will complain.
2. The string after PSK must be the same as that specified in psk.conf on Router_A.
Add the following lines in ipsec.conf: (This file defines among other things, the network to be protected, authentication methods, type of connection, etc.)
config setup interfaces="ipsec0=eth1" klipsdebug=none plutodebug=none uniqueids=yes conn %default keyingtries=0 authby=secret #rsasig conn crypt left=10.50.1.80 leftid=10.50.1.80 leftsubnet=10.1.13.1/24 right=10.50.1.3 rightid=10.50.1.3 rightsubnet=146.64.8.8/16 auto=start type=tunnel
NOTE: The name of our connection is called “crypt”. Under “config setup”, the line interfaces=”ipsec0=eth1” must refer to a real interface (ifconfig will show available interfaces) and also must be the interface through which the data to be protected will travel, in case of more than one NIC. The line “auto=start” says, the connection “crypt” must be brought up when openswan ipsec starts up; to bring up the connection manually either comment out the line or specify “auto=ignore”. The explanation given for ipsec.conf on Router_A is pretty much the same as for Router_B.
STARTING UP IPsec and Racoon (FreeBSD).
At this point all machines are able to reach (ping) each other successfully. Next ensure ipsec and racoon are not running. On my machine I do:
verdi2istc#/etc/rc.d/ipsec stop
Clearing ipsec manual keys/policies.
to stop ipsec if it was already running; and do
verdi2istc# setkey -P -D
No SPD entries.
To ensure there are no IPsec SA/SP database entries; and next do
verdi2istc#killall racoon
to stop racoon.
Next issue
verdi2istc# /etc/rc.d/ipsec restart
to start ipsec, and to verify ipsec started successfully then do
verdi2istd# setkey -P -D
10.1.13.0/24[any] 146.64.0.0/16[any] any
in ipsec
esp/tunnel/10.50.1.80-10.50.1.3/require
created: Aug 30 09:27:39 2005 lastused: Aug 30 09:27:39 2005
lifetime: 0(s) validtime: 0(s)
spid=16531 seq=1 pid=583
refcnt=1
146.64.0.0/16[any] 10.1.13.0/24[any] any
out ipsec
esp/tunnel/10.50.1.3-10.50.1.80/require
created: Aug 30 09:27:39 2005 lastused: Aug 30 09:27:39 2005
lifetime: 0(s) validtime: 0(s)
spid=16530 seq=0 pid=583
refcnt=1
From Router_A, type either racoon (to run in the backgroung) or racoon –F
verdi2istd#racoon
or to fun in foreground type
verdi2istd#racoon -F -d
Foreground mode.
2005-08-30 09:51:59: INFO: main.c:172:main(): @(#)package version freebsd-20040818a
2005-08-30 09:51:59: INFO: main.c:174:main(): @(#)internal version 20001216 sakane@kame.net
2005-08-30 09:51:59: INFO: main.c:175:main(): @(#)This product linked OpenSSL 0.9.7d 17 Mar 2004 (http://www.openssl.org/)
2005-08-30 09:51:59: DEBUG: pfkey.c:434:pfkey_init(): call pfkey_send_register for AH
2005-08-30 09:51:59: DEBUG: pfkey.c:434:pfkey_init(): call pfkey_send_register for ESP
2005-08-30 09:51:59: DEBUG: pfkey.c:434:pfkey_init(): call pfkey_send_register for IPCOMP
2005-08-30 09:51:59: DEBUG: cftoken.l:578:yycf_set_buffer(): reading config file /usr/local/etc/racoon/racoon.conf
2005-08-30 09:51:59: DEBUG: pfkey.c:2379:pk_checkalg(): compression algorithm can not be checked because sadb message doesn't support it.
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: 10.50.1.3 (ath0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: fe80::202:6fff:fe21:2e71%ath0 (ath0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: 146.64.8.1 (sis0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: fe80::200:24ff:fec2:b684%sis0 (sis0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: 127.0.0.1 (lo0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: ::1 (lo0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:206:grab_myaddrs(): my interface: fe80::1%lo0 (lo0)
2005-08-30 09:51:59: DEBUG: grabmyaddr.c:474:autoconf_myaddrsport(): configuring default isakmp port.
2005-08-30 09:52:00: DEBUG: grabmyaddr.c:496:autoconf_myaddrsport(): 7 addrs are configured successfully
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): fe80::1%lo0[500] used as isakmp port (fd=5)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): ::1[500] used as isakmp port (fd=6)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): 127.0.0.1[500] used as isakmp port (fd=7)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): fe80::200:24ff:fec2:b684%sis0[500] used as isakmp port (fd=8)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): 146.64.8.1[500] used as isakmp port (fd=9)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): fe80::202:6fff:fe21:2e71%ath0[500] used as isakmp port (fd=10)
2005-08-30 09:52:00: INFO: isakmp.c:1368:isakmp_open(): 10.50.1.3[500] used as isakmp port (fd=11)
2005-08-30 09:52:00: DEBUG: pfkey.c:197:pfkey_handler(): get pfkey X_SPDDUMP message
2005-08-30 09:52:00: DEBUG: pfkey.c:197:pfkey_handler(): get pfkey X_SPDDUMP message
2005-08-30 09:52:00: DEBUG: policy.c:184:cmpspidxstrict(): sub:0xbfbfea30: 146.64.0.0/16[0] 10.1.13.0/24[0] proto=any dir=out
2005-08-30 09:52:00: DEBUG: policy.c:185:cmpspidxstrict(): db :0x809dc08: 10.1.13.0/24[0] 146.64.0.0/16[0] proto=any dir=in
The –d option is for debug, to see more output add extra –d.
IMPORTANT: At this point if all went well Client_A should not be reachable (try ping) from Router_B and Client_B; meaning private LAN_A is now protected. However, Router_A and Router_B should be able reach/see each other. Do not continue until this is accomplished.
STARTING UP OPENSWAN IPSEC
Now, on Router_B do:
root@Lawrence:/# ipsec setup restart
ipsec_setup: Stopping Openswan IPsec...
ipsec_setup: Starting Openswan IPsec 2.3.1...
verify that the IPsec tunnel has been established correctly by issuing:
root@Lawrence:/# ipsec whack --status
000 interface ipsec0/eth1 10.50.1.80
000 %myid = (none)
000 debug none
000
000 algorithm ESP encrypt: id=3, name=ESP_3DES, ivlen=64, keysizemin=168, keysizemax=168
000 algorithm ESP encrypt: id=12, name=ESP_AES, ivlen=128, keysizemin=128, keysizemax=256
000 algorithm ESP auth attr: id=1, name=AUTH_ALGORITHM_HMAC_MD5, keysizemin=128, keysizemax=128
000 algorithm ESP auth attr: id=2, name=AUTH_ALGORITHM_HMAC_SHA1, keysizemin=160, keysizemax=160
000
000 algorithm IKE encrypt: id=7, name=OAKLEY_AES_CBC, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: id=5, name=OAKLEY_3DES_CBC, blocksize=8, keydeflen=192
000 algorithm IKE hash: id=2, name=OAKLEY_SHA1, hashsize=20
000 algorithm IKE hash: id=1, name=OAKLEY_MD5, hashsize=16
000 algorithm IKE dh group: id=2, name=OAKLEY_GROUP_MODP1024, bits=1024
000 algorithm IKE dh group: id=5, name=OAKLEY_GROUP_MODP1536, bits=1536
000 algorithm IKE dh group: id=14, name=OAKLEY_GROUP_MODP2048, bits=2048
000 algorithm IKE dh group: id=15, name=OAKLEY_GROUP_MODP3072, bits=3072
000 algorithm IKE dh group: id=16, name=OAKLEY_GROUP_MODP4096, bits=4096
000 algorithm IKE dh group: id=17, name=OAKLEY_GROUP_MODP6144, bits=6144
000 algorithm IKE dh group: id=18, name=OAKLEY_GROUP_MODP8192, bits=8192
000
000 stats db_ops.c: {curr_cnt, total_cnt, maxsz} :context={0,0,0} trans={0,0,0} attrs={0,0,0}
000
000 "crypt": 10.1.13.0/24===10.50.1.80...10.50.1.3===146.64.0.0/16; erouted; eroute owner: #2
000 "crypt": srcip=unset; dstip=unset
000 "crypt": ike_life: 3600s; ipsec_life: 28800s; rekey_margin: 540s; rekey_fuzz: 100%; keyingtries: 0
000 "crypt": policy: PSK+ENCRYPT+TUNNEL+PFS+UP; prio: 24,16; interface: eth1;
000 "crypt": newest ISAKMP SA: #1; newest IPsec SA: #2;
000 "crypt": IKE algorithm newest: 3DES_CBC_192-SHA1-MODP1024
000
000 #2: "crypt":500 STATE_QUICK_I2 (sent QI2, IPsec SA established); EVENT_SA_REPLACE in 27961s; newest IPSEC; eroute owner
000 #2: "crypt" esp.2ec9213@10.50.1.3 esp.aa7dc439@10.50.1.80 tun.1002@10.50.1.3 tun.1001@10.50.1.80
000 #1: "crypt":500 STATE_MAIN_I4 (ISAKMP SA established); EVENT_SA_REPLACE in 2625s; newest ISAKMP; nodpd
000
root@Lawrence:/#
At this point Client_A should be reachable by Client_B. On each/either Router do a tcpdump; and any packets with ESP indicates that the setup tunnel is currently handling data from the clients.
NOTE: ESP packets will only appear if there are packets from either client to the other client.
DEBUGGING (Openswan IPsec)
Earlier I showed how to stop a connection from being started up automatically by openswan. IPsec. So now with ipsec running but our connection “crypt” NOT up, we will debug the starting up of the connection (crypt). To debug the key exchange with racoon, first create a script with following content:
ipsec pluto --debug-all
ipsec whack \
--name crypt \
--tunnel \
--host 10.50.1.80 \
--nexthop 10.50.1.3 \
--client 10.1.13.1/24 \
--updown 'ipsec _updown' --id 10.50.1.80 \
--to \
--host 10.50.1.3 \
--client 146.64.8.1/16 \
--updown 'ipsec _updown' --id 10.50.1.3 \
--psk \
--esp 3des-md5,3des-sha1 \
--ike 3des-md5,3des-sha1 \
--encrypt
ipsec whack --listen
ipsec whack --route --name crypt
ipsec whack --initiate --name crypt
Running this script will show the various key exchange messages. The messages are pretty much clear to see what it’s happening.
HowTo stop DHCP client over-writing resolv.conf
Finally I found out how to do it
Edit the /etc/dhcp3/dhclient.conf file Find the line that says request
Comment out the line that requests for domain-name, domain-name-servers and host-name
request subnet-mask, broadcast-address, time-offset, routers, # domain-name, domain-name-servers, host-name, netbios-name-servers, netbios-scope;
HowTo setup DHCP with OLSR
There have been so many misleading postings on this - I will finally set the record straight.
You will need to reserve a block of IP's for non OLSR wireless clients that want to connect onto the mesh network such as a laptop. Here is an example setup:
Wireless router 1: Wireless IP: 10.51.1.13 LAN IP: 10.3.13.1 Subnet for Wireless DHCP clients: 10.51.1.64/28 (This would mean that 16 machines could potentially connect to this wireless router. The IP leases will be in the range from 10.51.1.64 to 10.51.1.79)
Wireless router 2: Wireless IP: 10.51.1.14 LAN IP: 10.3.14.1 Subnet for Wireless DHCP clients : 10.51.1.80/28 (IP leases will be in the range from 10.51.1.80 to 10.51.1.93)
To set this up On Friefunk firmware Wireless Router 1: OLSR: OLSR DHCP: 10.51.1.64/28
Wireless Router 2: OLSR: OLSR DHCP: 10.51.1.80/28
Most people gave strange values for OLSR DHCP in their postings the most common one was:
OLSR DHCP: 10.51.1.80/28, 255.255.255.240
The subnet mask after the comma (255.255.255.240) is an alternative to the slash format /28. Why does everyone have this reduntant subnet mask on their postings???
Linux HowTos
HowTo setup your own network profiles on a laptop
I have always wanted to write some good scripts that configure my laptop for home and work wireless/ethernet automatically in ubuntu and so I set about building up a set of scripts that I can call.
I have four scenarios: 1. use laptop at home with wireless access point 2. use laptop at home with ethernet 3. use laptop at work with wireless access point 4. use laptop at work with ethernet
I created two files in /etc/network: interfaces.work and interfaces.home with all the ethernet and wireless settings for home and work in this file
/etc/network/interfaces.home
- This file describes the network interfaces available on your system
- and how to activate them. For more information, see interfaces(5).
- The loopback network interface
auto lo iface lo inet loopback
- The primary network interface
iface eth0 inet static address 10.3.13.102 netmask 255.255.255.0 gateway 10.3.13.1
- The wireless network interface
iface eth1 inet dhcp wireless-essid pta-mesh wireless-mode Ad-Hoc wireless-channel 1 wireless-key off
/etc/network/interfaces.work
- This file describes the network interfaces available on your system
- and how to activate them. For more information, see interfaces(5).
- The loopback network interface
auto lo iface lo inet loopback
- The primary network interface
iface eth0 inet dhcp
- The wireless network interface
iface eth1 inet dhcp wireless-essid icomtek wireless_mode Managed wireless-key off
I also created two files with my dns and domain settings for home and work in /etc/ called resolv.home and resolv.work
resolv.home search icomtek.csir.co.za elarduspark.org.za cids.org.za nameserver 146.64.28.1 10.3.13.1
resolv.work search icomtek.csir.co.za cids.org.za nameserver 146.64.28.1
Here are my scripts that configure my interfaces based on the above files
1. Setup for wireless networking at home /usr/local/bin/homenet-wireless
- !/bin/bash
echo Setting up network for home wireless network sudo cp /etc/network/interfaces.home /etc/network/interfaces
eth0_status=`ifconfig | grep eth0` eth1_status=`ifconfig | grep eth1`
if [ -n "$eth0_status" ]; then sudo ifdown eth0 fi
if [ -n "$eth1_status" ]; then sudo ifdown eth1 fi
sudo ifup eth1
sudo cp /etc/resolv.home /etc/resolv.conf
2. Setup for ethernet networking at home /usr/local/bin/homenet-fixed
- !/bin/bash
echo Setting up network for home ethernet sudo cp /etc/network/interfaces.home /etc/network/interfaces sudo cp /etc/resolv.home /etc/resolv.conf
eth0_status=`ifconfig | grep eth0` eth1_status=`ifconfig | grep eth1`
if [ -n "$eth0_status" ]; then sudo ifdown eth0 fi
if [ -n "$eth1_status" ]; then sudo ifdown eth1 fi
sudo ifup eth0
3. Setup for wireless at work /usr/local/bin/worknet-wireless
- !/bin/bash
echo Setting up network for work wireless network sudo cp /etc/network/interfaces.work /etc/network/interfaces sudo cp /etc/resolv.work /etc/resolv.conf
eth0_status=`ifconfig | grep eth0` eth1_status=`ifconfig | grep eth1`
if [ -n "$eth0_status" ]; then sudo ifdown eth0 fi
if [ -n "$eth1_status" ]; then sudo ifdown eth1 fi
sudo ifup eth1
4. Setup for ethernet at work /usr/local/bin/worknet-fixed
- !/bin/bash
echo Setting up network for work ethernet sudo cp /etc/network/interfaces.work /etc/network/interfaces sudo cp /etc/resolv.work /etc/resolv.conf
eth0_status=`ifconfig | grep eth0` eth1_status=`ifconfig | grep eth1`
if [ -n "$eth0_status" ]; then sudo ifdown eth0 fi
if [ -n "$eth1_status" ]; then sudo ifdown eth1 fi
sudo ifup eth0
HowTo Setup a Linux machine to become an access point
1. Make sure you install dhcpd off the Mandrake disks
2. Put the Wireless card into access point mode with the following example script /etc/sysconfig/network-scripts/ifcfg-wifi0
DEVICE=wifi0 BOOTPROTO=static IPADDR=192.168.0.1 ONBOOT=yes NETMASK=255.255.255.0 NETWORK=192.168.0.0 BROADCAST=192.168.0.255 DHCP_TIMEOUT=5 WIRELESS_MODE=Master WIRELESS_ESSID=mesh WIRELESS_CHANNEL=10
3. run ifup wifi0
4. copy /etc/dhcpd.conf.sample (this file only exisits the first time you install dhcpd) to dhcpd.conf ... Change the IP address allocations in this file to suite your needs
5. start dhcpd with /etc/rc.d/init.d/dhcpd
6. Check the /var/lib/dhcpd/dhcpd.leases to check which IP addresses are being assigned
HowTo Set up the SENOA card in linux
1. Download the hostap driver from ftp://edna.icomtek.csir.co.za/pub/drivers ... This driver ensures that the SENOA card can run in Access point mode as well as Ad-Hoc and Infrastructure
2. Unzip using gunzip < hostap-driver-0.2.4.tar.gz | tar xvf -
3. Change Makefile to include KERNEL_PATH ... KERNEL_PATH=/usr/src/linux
4. Run 'make'
5. run 'make install'
6. Restart card manager using /etc/rc.d/init.d/pcmcia restart
If you are using the PCI to PCMCIA bridge card with the RLSC475 chipset follow these steps
1. Edit the file /etc/sysconfig/pcmcia to include these lines
PCMCIA=yes PCIC=RLSC475
2. Run /etc/rc.d/init.d/pcmcia restart
Linux network configurations tips
1. Setting IP address and modes of interface
The file /etc/sysconfig/network-scripts/ifcfg-eth0 contains all the settingsfor interface eth0 including
IP allocation type (static or dynamic) IP Address Subnet mask Broadcast address Wireless mode wireless channel
type
# man ifcfg
to see all the options for this config file
Use
# ifup eth0
to bring eth0 network interface up using the script ifcfg-eth0
#ifdown eth0
to pull the eth0 interface down
2. The DNS nameserver
The file /etc/resolve.conf contains the nameserver (dns) to use for the network
3. The gateway and other network routes
To see the current network routes type
# route
This will show you all the routes which the network is currently using
To add a new route for interface eth0 type
# route add -net 10.0.0.0 netmask 255.255.255.0 dev eth0
This adds a route to the network 10.0.0.0 using device eth0
# route add default gw 10.0.0.8
Adds a default route which will be used if no other route matches.
There should be an existing route, in this case, to 10.0.0.8 through some interface.
HowTo use the freespace loss equation
From: Radio theory and link planning for Wireless LAN (WLAN)
Everyone should know the free space loss equation in their head
Loss [ dB] = 32.44 + 20(Log(distance[km]) + Log(freq[MHz]))
Useful cable losses
RG58 = 1 dB/m RG213 = -.6 dB/m RG174 = 2 dB/m (often used in pigtails) LMR-400 = 0.22 dB/m
Typical WiFi sensitivity for orinoco cards
11Mbps = -82dBm 5.5Mbps = -87dBm 2Mbps = -92dBm 1Mbps = -94dBm
Typical allowed signal to noise ratios for orinoco cards
11Mbps = 16dB 5.5Mbps = 11dB 2Mbps = 7dB 1Mbps = 4dB
Typical Noise level at 2.4GHz = -100dBm. Compute S/N level eg. at 11Mbps = -84dBm but sensitivity is -82dBm so sensitivity is the limiting factor.
Just worked out that with our 2 8dBi omnis, 2dB loss in the RF cable each side of the link and the 200mW SENOA cards it is possible to acheive a theoretical distance of 5km with a 3dB margin (margin probably a bit tight), 4km will give you a 5dB margin - probably more realistic.